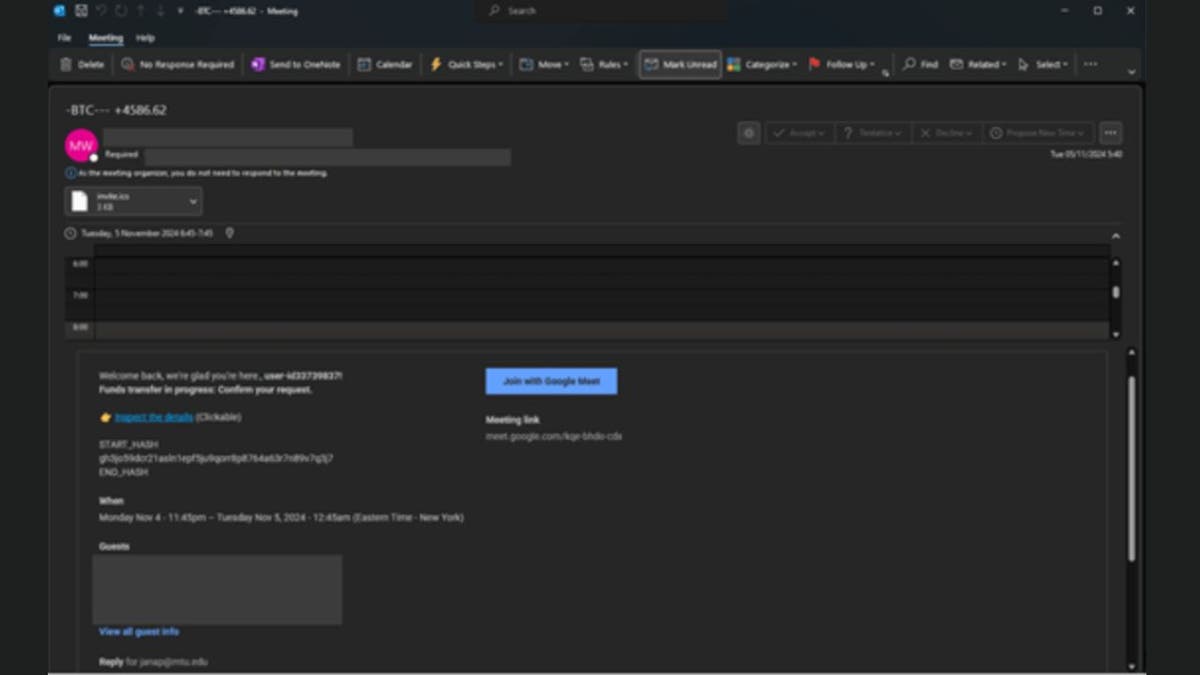
Tech support scams have been around for years, but a new variant called the Phantom Hacker scam is rapidly gaining traction. It has cost victims, primarily older Americans, over $500 million since 2023. This scam is particularly deceptive because it unfolds in three carefully orchestrated phases and uses AI-powered social engineering tactics to avoid detection. Attackers leverage caller ID spoofing and AI-generated voices to make their scheme more persuasive, but there are ways to protect yourself.
Stay protected & informed! Get security alerts & expert tech tips—sign up for Kurt’s The CyberGuy Report now.
Illustration of a phantom hacker at work (Kurt “CyberGuy” Knutsson)
How the phantom hacker scam works
As highlighted by the FBI, the scam begins with the tech support impostor phase. You might receive a call, email, text or even a pop-up on your computer warning you that your device has been compromised. The message urges you to call a customer support number for assistance. Once you do, a scammer posing as tech support claims that hackers have targeted your accounts. To “help,” they instruct you to download remote access software, allowing them to take control of your computer. Under the guise of scanning for threats, they trick you into revealing your financial accounts, setting up the next phase of the scam.
Next comes the financial institution impostor phase. Another scammer, pretending to be from your bank or investment firm, calls to warn that a foreign hacker has infiltrated your accounts. They advise moving your money to a “safe” government-protected account, often using wire transfers, cryptocurrency or cash deposits. They might also insist on keeping the transaction confidential, claiming it’s necessary for security reasons.
In the final U.S. government impostor phase, a third scammer impersonates a federal official – often from the Federal Reserve – who pressures you to act quickly. If you start doubting the scheme, they may send you an official-looking email or document to convince you that the transfer is legitimate. By the time victims realize they’ve been tricked, their money is gone, often sent overseas beyond the reach of U.S. authorities.

Illustration of a phantom hacker at work (Kurt “CyberGuy” Knutsson)
SPOTIFY PLAYLISTS ARE BEING HIJACKED TO PROMOTE PIRATED SOFTWARE AND SCAMS
How AI is making things worse
AI is making scams like the Phantom Hacker scam more deceptive and harder to spot. Scammers are using AI-powered chatbots to automate their schemes. Instead of relying on human operators, they can now deploy AI-driven responses that sound natural and convincing.
AI-generated deepfake voices are also being used to impersonate bank officials and government representatives. With just a short audio sample, scammers can clone a voice to make their calls seem even more authentic. This means a victim might hear what sounds like their bank manager or an official from the Federal Reserve.
Email scams are also becoming more sophisticated. AI tools can craft messages that mimic the tone and style of official communications. Scammers can even generate fake but realistic-looking documents with official letterheads to convince victims that the scam is legitimate.

Illustration of man getting a deepfake scam call (Kurt “CyberGuy” Knutsson)
9 WAYS SCAMMERS CAN USE YOUR PHONE NUMBER TO TRY TO TRICK YOU
7 ways to protect yourself
The best way to defend yourself against the Phantom Hacker scam is to stay informed, be cautious and follow these steps:
1) Ignore unsolicited messages: Scammers often send pop-ups, text messages or emails claiming that your computer is infected or that your bank account is at risk. These messages may look official, but they are designed to create panic and pressure you into taking immediate action. Never click on links or attachments from unknown senders, as they may contain malware or lead to phishing websites that steal your personal information.
2) Have strong antivirus software: The best way to safeguard yourself from malicious links that install malware, potentially accessing your private information, is to have antivirus software installed on all your devices. This protection can also alert you to phishing emails and ransomware scams, keeping your personal information and digital assets safe. Get my picks for the best 2025 antivirus protection winners for your Windows, Mac, Android and iOS devices.
3) Verify phone numbers before calling: If you receive an unexpected message urging you to call tech support, do not use the number provided in the message. Instead, visit the official website of the company in question and find their customer support contact information. Scammers often create fake websites or use caller ID spoofing to make their phone numbers appear legitimate, so always double-check before making a call.
4) Avoid downloading unknown software: No reputable company will ever ask you to install remote access tools unless you have specifically reached out for tech support. Scammers use these programs to take control of your computer, monitor your activity and access sensitive information. If someone unexpectedly asks you to download software to “fix a problem” or “protect your account,” it is likely a scam.
5) Never give control of your device to a stranger: If you allow a scammer to remotely access your computer, they can view your personal files, log your keystrokes and manipulate your accounts without your knowledge. Legitimate customer support representatives will never request remote access unless you have initiated the support request through an official company channel. If someone insists on taking control of your device, hang up immediately.
6) Be skeptical of urgent financial warnings: The U.S. government will never contact you unexpectedly and demand that you move your money to a “safe account.” They will also never ask you to wire funds, purchase gift cards or send cryptocurrency as a form of payment. Scammers create a false sense of urgency to trick victims into acting before they can think critically about the situation. If someone claims to be from a bank or government agency and pressures you to move money, stop and verify their identity through official channels.
7) Invest in personal data removal services: Scammers often gather information from data broker websites to make their scams more convincing. Your name, phone number, home address and even financial history may be publicly available without your knowledge. Consider using a data removal service to regularly scan and request the removal of your personal information from these databases. This reduces the chances of scammers targeting you with highly personalized attacks. You can also manually opt out of major data broker sites, but using a service automates the process and keeps your information protected over time. Check out my top picks for data removal services here.
SUBSCRIBE TO KURT’S YOUTUBE CHANNEL FOR QUICK VIDEO TIPS ON HOW TO WORK ALL OF YOUR TECH DEVICES
Kurt’s key takeaway
The Phantom Hacker scam is designed to be convincing, but understanding how it works can help you stay one step ahead. Scammers rely on fear, urgency and deception to trick their victims, but you can protect yourself by staying cautious, verifying requests through official sources and never sharing personal or financial information with unknown callers.
Do you think law enforcement and tech companies are doing enough to combat AI-powered scams? Let us know by writing us at Cyberguy.com/Contact.
For more of my tech tips and security alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter.
Ask Kurt a question or let us know what stories you’d like us to cover.
Follow Kurt on his social channels:
Answers to the most asked CyberGuy questions:
New from Kurt:
Copyright 2025 CyberGuy.com. All rights reserved.