Every tech expert will tell you the App Store is safer than Google Play Store. Some might even claim it is impossible to download a malicious app from the App Store, but they are wrong.
While I admit the App Store is a secure and tightly controlled ecosystem, it cannot completely shield you. Security researchers have found that hackers are targeting several apps on the App Store to spread malware that steals information from screenshots saved on a device.
The issue also affects those downloading apps from the Google Play Store.
STAY PROTECTED & INFORMED! GET SECURITY ALERTS & EXPERT TECH TIPS — SIGN UP FOR KURT’S THE CYBERGUY REPORT NOW
A person holding an iPhone. (Kurt “CyberGuy” Knutsson )
How the malware works and what makes it different
According to researchers at Kaspersky, this malware campaign is more advanced than typical info stealers, both in how it works and how it spreads. Instead of relying on social engineering tricks to get users to grant permissions like most banking trojans or spyware, this malware hides inside seemingly legitimate apps and slips past Apple and Google’s security checks.
One of its standout features is Optical Character Recognition. Instead of stealing stored files, it scans screenshots saved on the device, extracts text and sends the information to remote servers.
Once installed, the malware operates stealthily, often activating only after a period of dormancy to avoid raising suspicion. It employs encrypted communication channels to send stolen data back to its operators, making it difficult to trace. Plus, it spreads through deceptive updates or hidden code within app dependencies, an approach that helps it evade initial security screenings by app store review teams.
The infection vectors vary between Apple and Google’s ecosystems. On iOS, the malware is often embedded within apps that initially pass Apple’s rigorous review process but later introduce harmful functionality through updates. On Android, the malware can exploit sideloading options, but even official Google Play apps have been found to carry these malicious payloads, sometimes hidden within SDKs (software development kits) supplied by third-party developers.
Messaging app in the App Store designed to lure victims.
THE HIDDEN COSTS OF FREE APPS: YOUR PERSONAL INFORMATION
What’s being stolen, and who’s responsible?
The scope of stolen information is alarming. This malware primarily targets crypto wallet recovery phrases but is also capable of exfiltrating login credentials, payment details, personal messages, location data and even biometric identifiers. Some versions are designed to harvest authentication tokens, allowing attackers to access accounts even if users change their passwords.
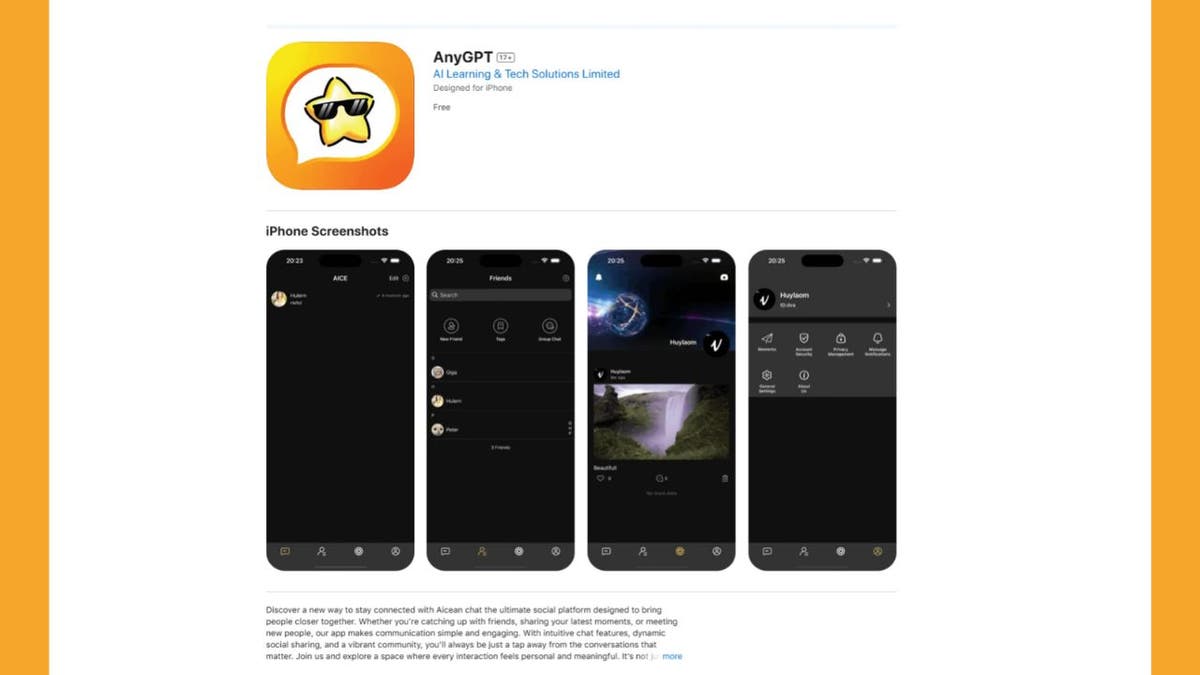
The apps serving as malware carriers include ComeCome, ChatAi, WeTink, AnyGPT and more. These range from productivity tools to entertainment and utility apps. In some cases, malicious developers create these apps with full knowledge of the malware’s purpose. In others, the issue appears to be a supply chain vulnerability, where legitimate developers unknowingly integrate compromised SDKs or third-party services that introduce malicious code into their applications.
We reached out to Apple for a comment but did not hear back before our deadline.
Messaging app in the App Store designed to lure victims. (Kaspersky)
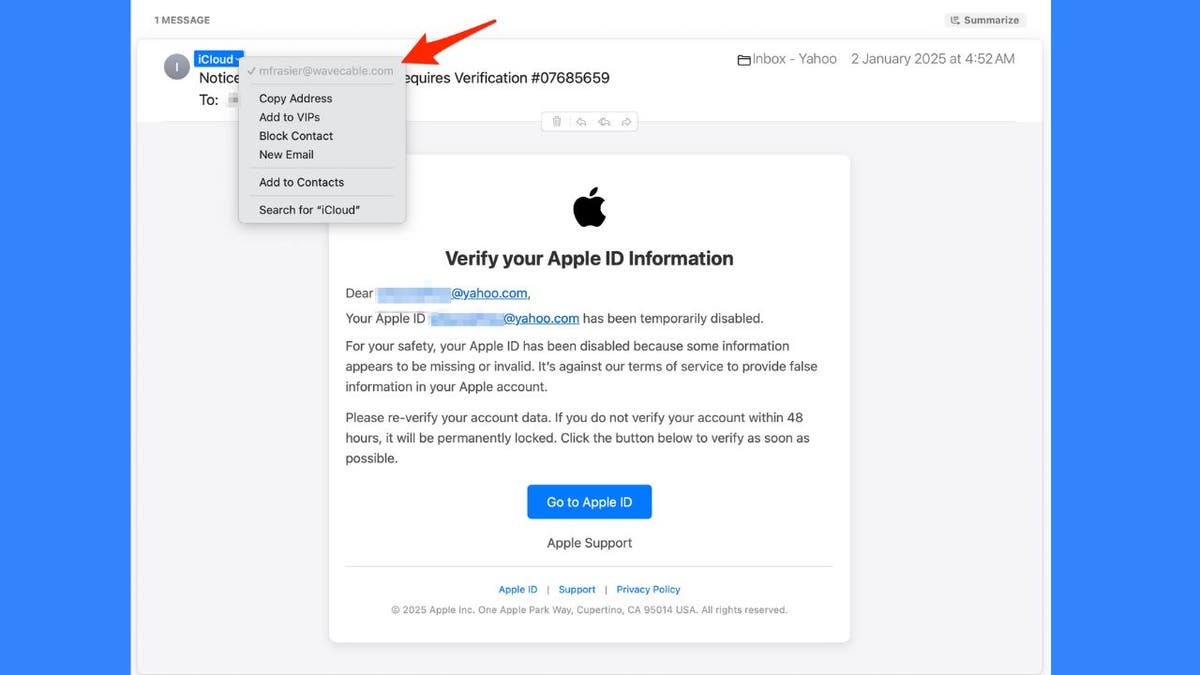
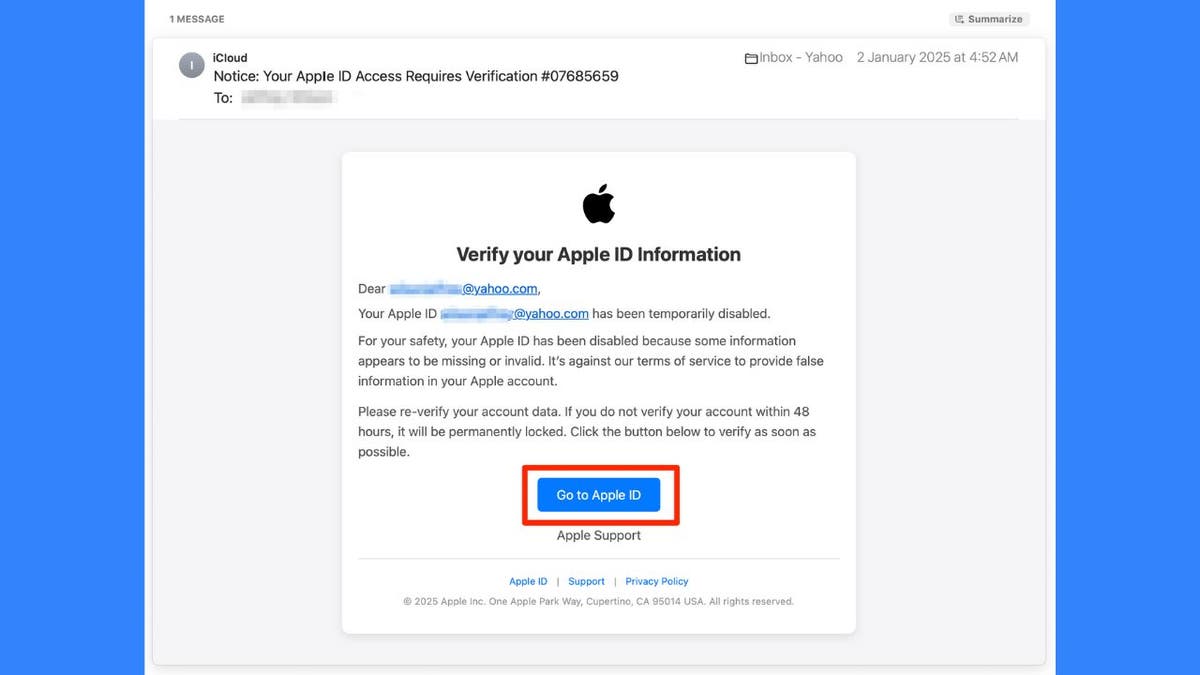
Apple’s response to screenshot-scanning malware discovered in App Store
Apple has removed the 11 iOS apps mentioned in Kaspersky’s report from the App Store. Furthermore, they discovered that these 11 apps shared code signatures with 89 other iOS apps, all of which had been previously rejected or removed for violating Apple’s policies, resulting in the termination of their developer accounts.
Apps requesting access to user data such as Photos, Camera or Location must provide relevant functionality or face rejection. They must also clearly explain their data usage when prompting users for permission. iOS privacy features ensure users always control whether their location information is shared with an app. Also, starting in iOS 14, the PhotoKit API — which allows apps to request access to a user’s Photos library — added additional controls to let users select only specific photos or videos to share with an app instead of providing access to their entire library.
The App Store Review Guidelines mandate that developers are responsible for ensuring their entire app, including ad networks, analytics services and third-party SDKs, complies with the guidelines. Developers must carefully review and choose these components. Apps must also accurately represent their privacy practices, including those of the SDKs they use, in their privacy labels.
In 2023, the App Store rejected over 1.7 million app submissions for failing to meet its stringent privacy, security and content standards. It also rejected 248,000 app submissions found to be spam, copycats or misleading and prevented 84,000 potentially fraudulent apps from reaching users.
WHAT IS ARTIFICIAL INTELLIGENCE (AI)?
What Google is doing to stop malware
A Google spokesperson tells CyberGuy:
“All of the identified apps have been removed from Google Play and the developers have been banned. Android users are automatically protected from known versions of this malware by Google Play Protect, which is on by default on Android devices with Google Play Services.”
However, it is important to note that Google Play Protect may not be enough. Historically, it isn’t 100% foolproof at removing all known malware from Android devices. Here’s why:
What Google Play Protect can do:
- Scans apps from the Google Play Store for known threats.
- Warns you if an app behaves suspiciously.
- Detects apps from unverified sources (sideloaded APKs).
- Can disable or remove harmful apps.
What Google Play Protect can’t do:
- It does not provide real-time protection against advanced threats like spyware, ransomware or phishing attacks.
- It does not scan files, downloads or links outside of Play Store apps.
- It may miss malware from third-party app stores or sideloaded apps.
- It lacks features like VPN protection, anti-theft tools and privacy monitoring.
Image of a person typing in their password on screen. (Kurt “CyberGuy” Knutsson)
HOW SCAMMERS USE YOUR PERSONAL DATA FOR FINANCIAL SCAMS AND HOW TO STOP THEM
5 ways users can protect themselves from such malware
1. Use strong antivirus software: Installing strong antivirus software can add an extra layer of protection by scanning apps for malware, blocking suspicious activity and alerting you to potential threats. The best way to safeguard yourself from malicious links that install malware, potentially accessing your private information, is to have antivirus software installed on all your devices. This protection can also alert you to phishing emails and ransomware scams, keeping your personal information and digital assets safe. Get my picks for the best 2025 antivirus protection winners for your Windows, Mac, Android and iOS devices.
2. Stick to trusted developers and well-known apps: Even though malware has been found in official app stores, users can still minimize their risk by downloading apps from reputable developers with a long track record. Before installing an app, check its developer history, read multiple reviews and look at the permissions it requests. If an app from an unknown developer suddenly gains popularity but lacks a strong review history, approach it with caution.
GET FOX BUSINESS ON THE GO BY CLICKING HERE
3. Review app permissions carefully: Many malicious apps disguise themselves as legitimate tools but request excessive permissions that go beyond their stated purpose. For example, a simple calculator app should not need access to your contacts, messages or location. If an app asks for permissions that seem unnecessary, consider it a red flag and either deny those permissions or avoid installing the app altogether. Go to your phone settings and check app permissions on your iPhone and Android.
4. Keep your device and apps updated: Cybercriminals exploit vulnerabilities in outdated software to distribute malware. Always keep your operating system and apps updated to the latest versions, as these updates often contain critical security patches. Enabling automatic updates ensures that you stay protected without having to manually check for new versions.
5. Be wary of apps that promise too much: Many malware-infected apps lure users by offering features that seem too good to be true — such as free premium services, extreme battery optimizations or AI-powered functionality that appears unrealistic. If an app’s claims sound exaggerated or its download numbers skyrocket overnight with questionable reviews, it’s best to avoid it. Stick to apps with a transparent development team and verifiable functionalities.
HOW TO REMOVE YOUR PRIVATE DATA FROM THE INTERNET
Kurt’s key takeaway
The new malware campaign highlights the need for stricter vetting processes, continuous monitoring of app behavior post-approval and greater transparency from app stores regarding security risks. While Apple and Google have removed the malicious apps upon detection, the fact that they made it onto the platform in the first place exposes a gap in the existing security framework. As cybercriminals refine their methods, app stores must evolve just as quickly or risk losing the trust of the very users they claim to protect.
CLICK HERE TO GET THE FOX NEWS APP
Do you think app stores should take more responsibility for malware slipping through? Let us know by writing us at Cyberguy.com/Contact
For more of my tech tips and security alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter
Ask Kurt a question or let us know what stories you’d like us to cover.
Follow Kurt on his social channels:
Answers to the most-asked CyberGuy questions:
New from Kurt:
Copyright 2025 CyberGuy.com. All rights reserved.
Kurt “CyberGuy” Knutsson is an award-winning tech journalist who has a deep love of technology, gear and gadgets that make life better with his contributions for Fox News & FOX Business beginning mornings on “FOX & Friends.” Got a tech question? Get Kurt’s free CyberGuy Newsletter, share your voice, a story idea or comment at CyberGuy.com.