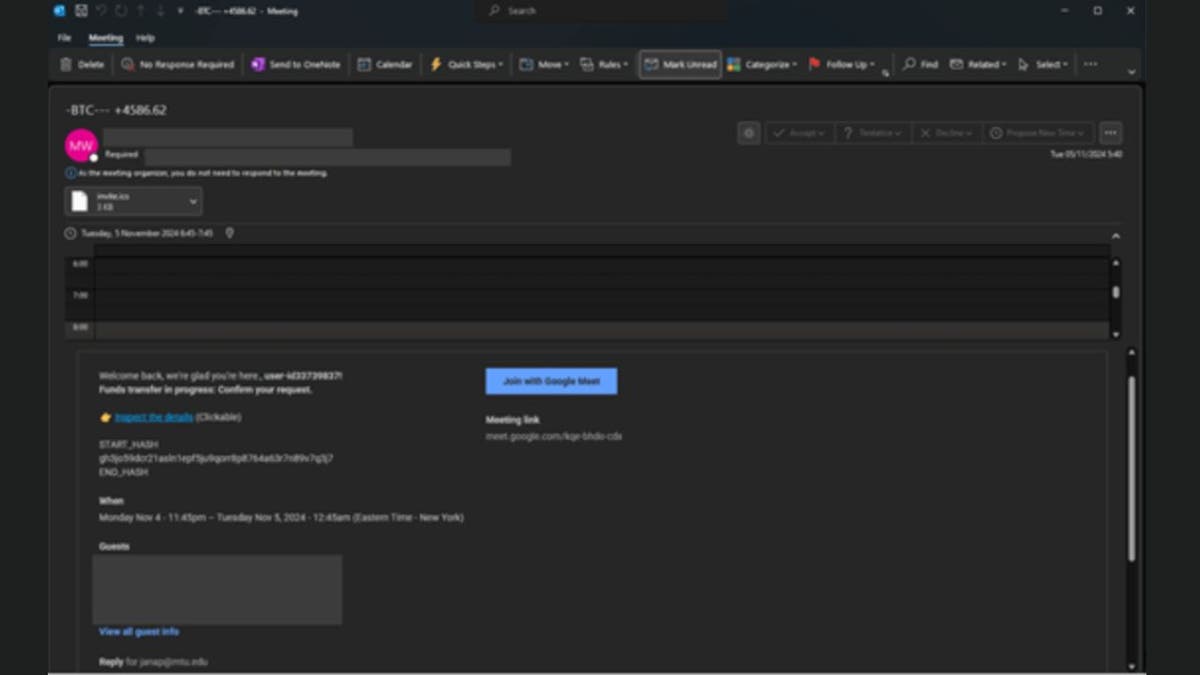
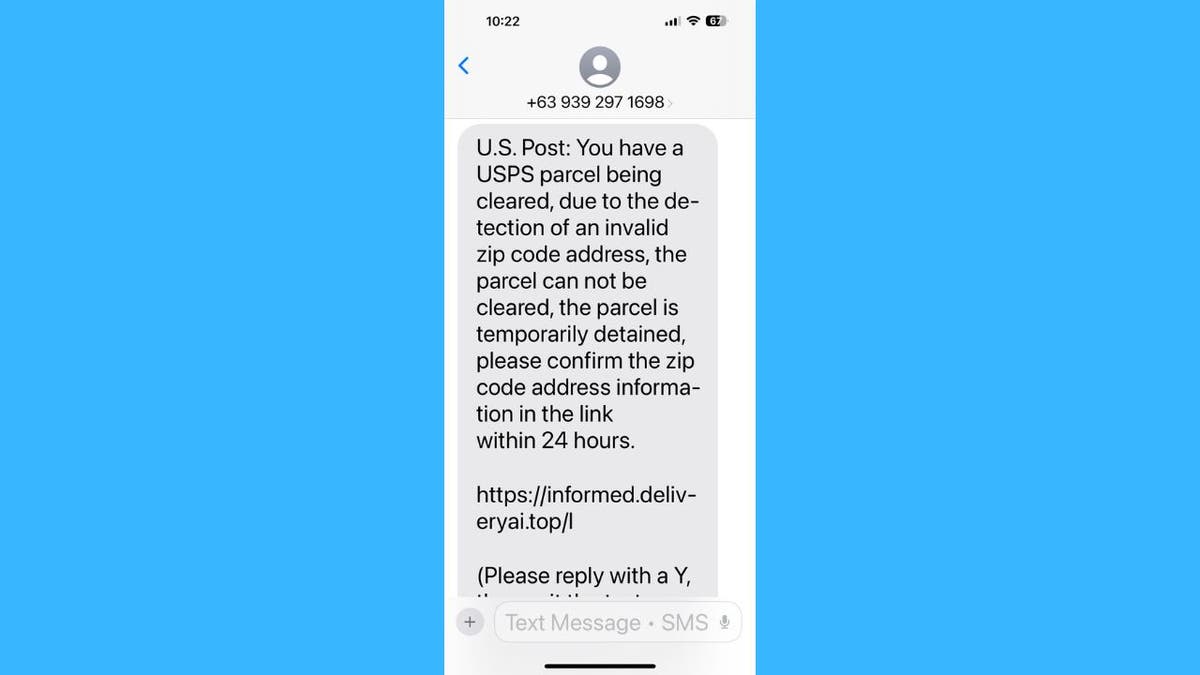
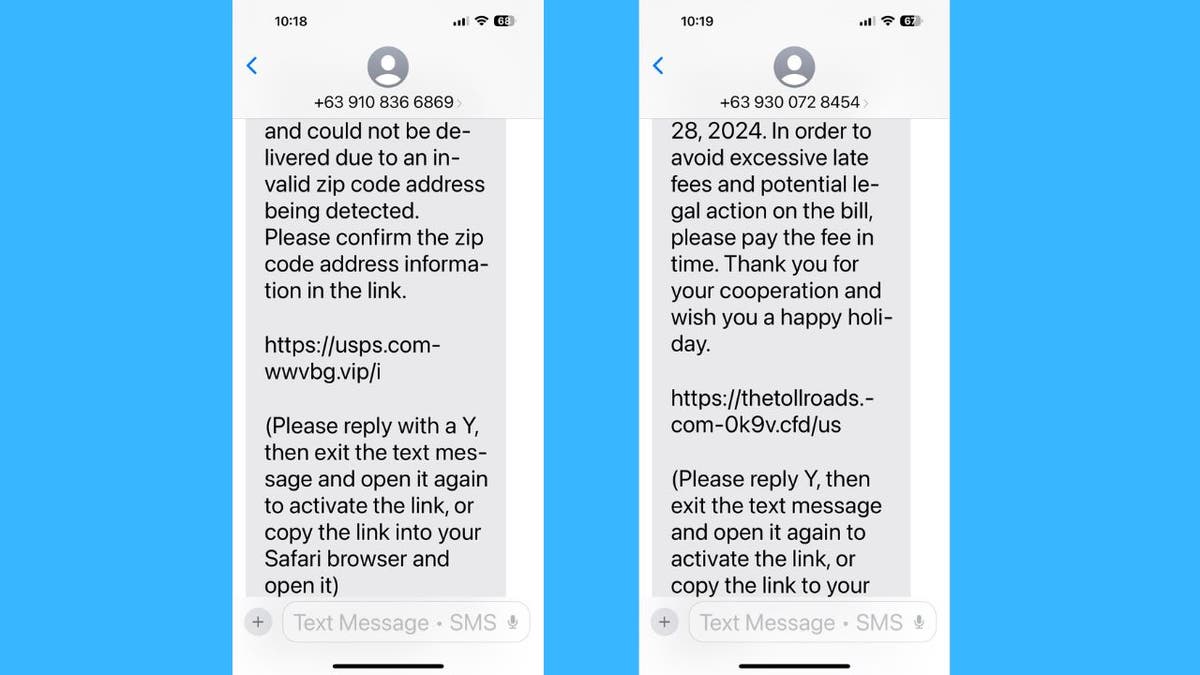
Almost everything you do online asks for your email. If you have been using the same one for a while, chances are hundreds or even thousands of services have it. They send promotional messages, social media alerts, newsletters and more, turning your inbox into complete chaos. You can tame this madness using an email alias.
An email alias helps declutter your inbox by organizing emails based on their purpose. For example, you can create specific aliases for shopping, newsletters or work and set up filters to sort these messages into separate folders automatically.
Aliases also help manage spam. If an alias starts receiving too many unwanted messages, you can disable it without affecting your main email.
Let’s dive into how to create an email alias on different platforms, including Gmail, Outlook and iCloud.
I’M GIVING AWAY THE LATEST & GREATEST AIRPODS PRO 2
A person setting up an alias email (Kurt “CyberGuy” Knutsson)
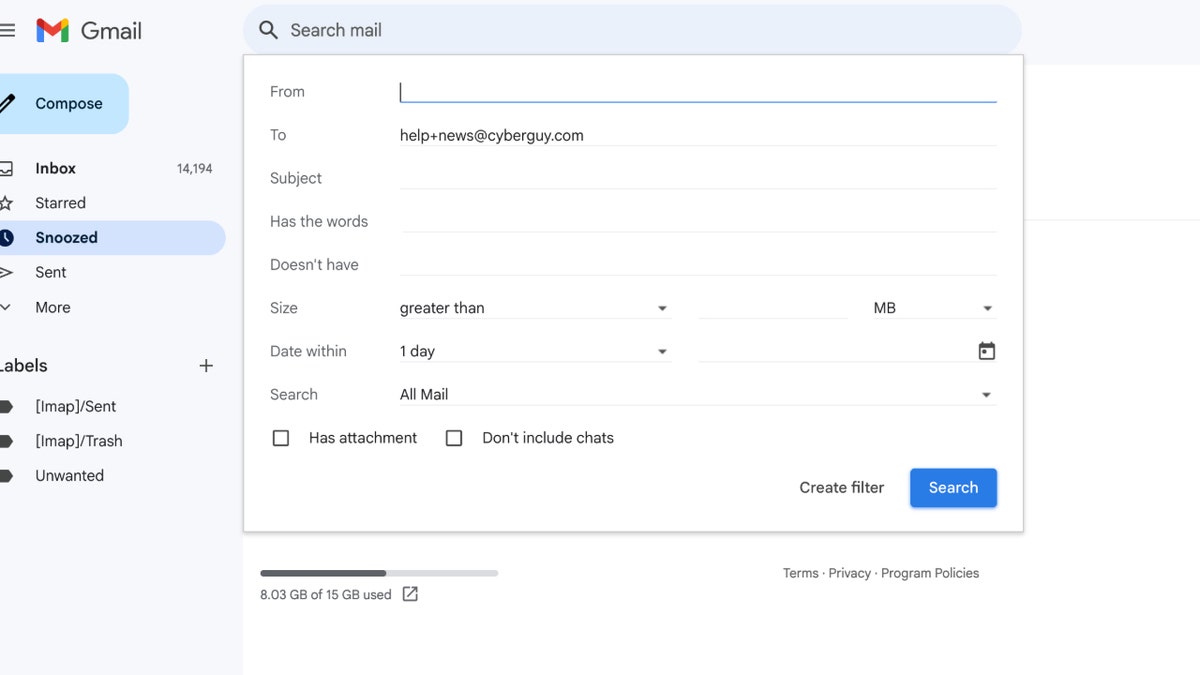
How to create an alias using Gmail
Gmail doesn’t allow you to create a completely separate alias, but it offers workarounds using “+ addressing” or by adding dots to your existing email address. However, these methods don’t prevent an unscrupulous sender from seeing your primary address, so exercise caution when using them with untrusted correspondents. Follow the steps below to get started.
Option 1: Create an alias using the ‘plus (+) trick’
Use your existing Gmail address and add a “+” followed by any keyword before “@gmail.com.”
Example: If your email is [email protected], you can use:
No additional setup is needed, just start using this alias when signing up for services or sharing your email.
Option 2: Create an alias using the ‘dot (.) trick’
Gmail ignores dots (.) in email addresses, so you can create variations of your email:
Example: If your email is [email protected], you can use:
All variations will deliver emails to your main inbox automatically.
Setting up an alias on Gmail (Kurt “CyberGuy” Knutsson)
MASSIVE SECURITY FLAW PUTS MOST POPULAR BROWSERS AT RISK ON MAC
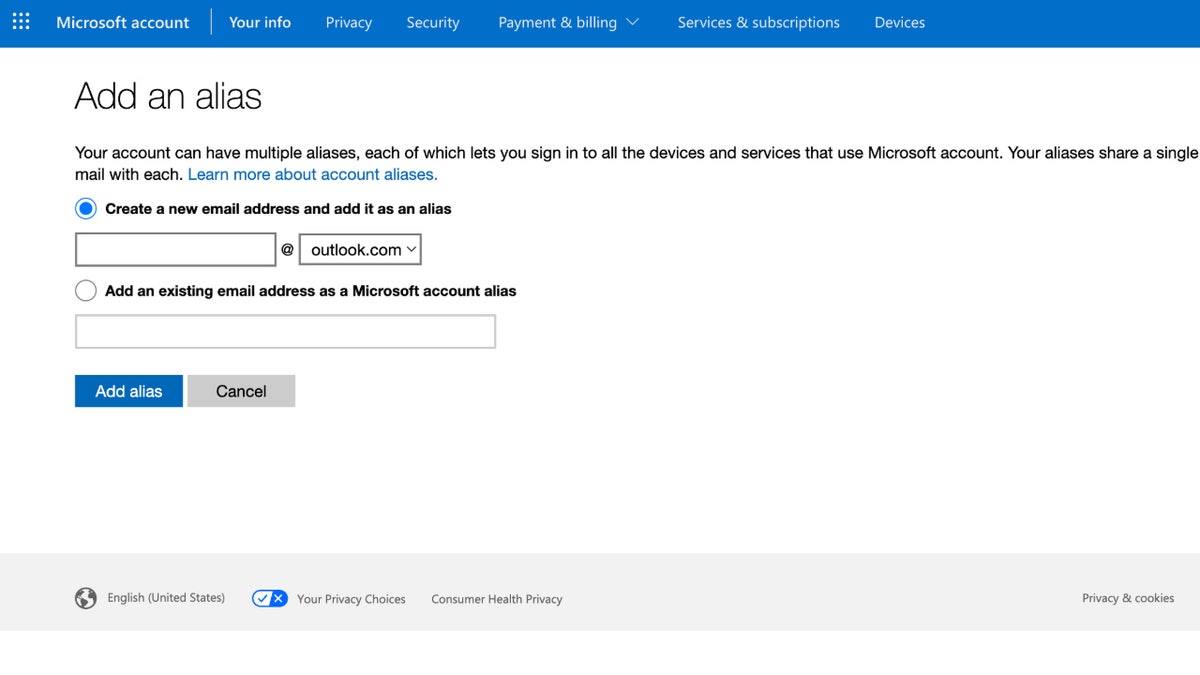
How to create an alias in Outlook.com
Outlook.com allows you to create additional email addresses (aliases) that are linked to your primary account. Emails sent to an alias will arrive in your primary inbox, and you can send messages using the alias as well.
Example:
If your primary email is [email protected], you can create an alias like [email protected]. Emails sent to [email protected] will still go to [email protected], but you can choose to send emails using either address.
Steps to create an alias:
- Sign in to your Outlook.com account
- Click the gear icon in the upper-right corner to open Settings
- Scroll down and select View all Outlook settings
- Navigate to Mail
- Then click Sync email
- Click Manage or choose a primary alias under Account alias
- Select Add email and follow the prompts to create your new alias
- Choose whether to create a new Outlook.com email as an alias or use an existing email (non-Outlook) as an alias
- Click Add alias to confirm
WHAT IS ARTIFICIAL INTELLIGENCE (AI)?
Once added, you can send emails using your alias by selecting it in the From field when composing a new message.
Important limitations to note:
- You can add up to 10 aliases in total
- There’s a limit of 10 new aliases that can be created in one year
- You can only add two aliases per week
- Existing Hotmail, Live, Outlook.com and MSN addresses can’t be added as aliases
- Aliases can only contain letters, numbers, dots (.), underscores (_) or hyphens (-)
- It’s no longer possible to create new aliases with @hotmail, @live.com or @msn.com domains
Setting up an alias using Outlook.com (Kurt “CyberGuy” Knutsson)
HOW TO REMOVE YOUR PRIVATE DATA FROM THE INTERNET
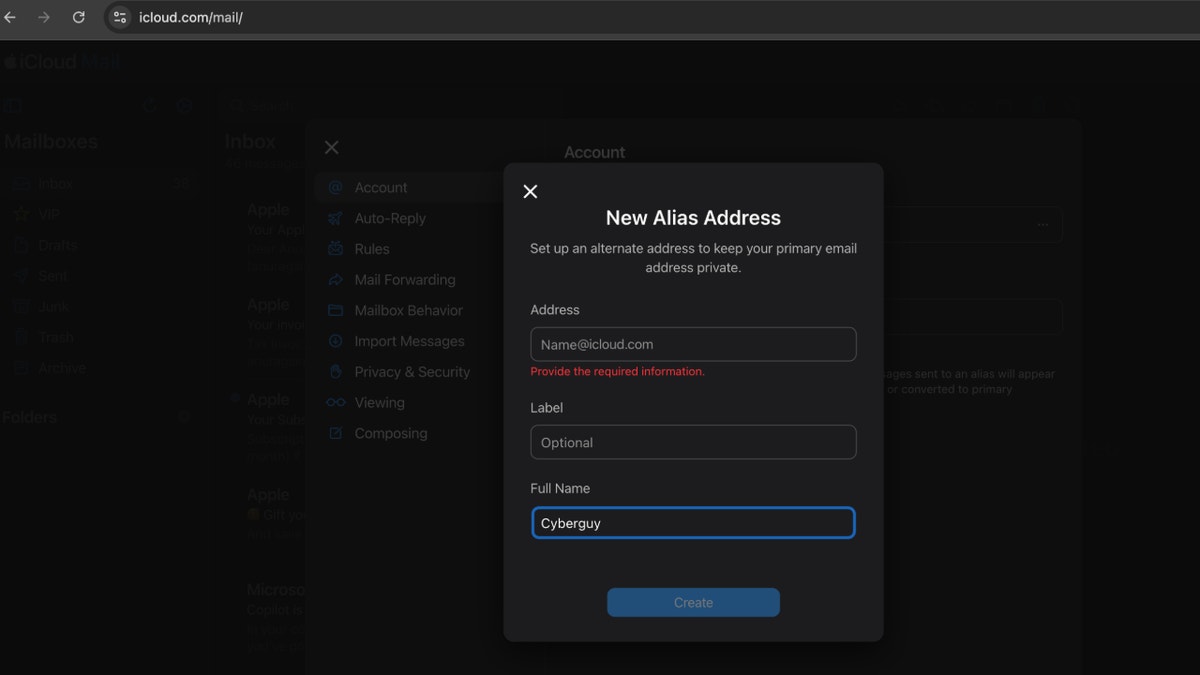
How to create an alias using your Apple ID
Apple allows you to create up to three email aliases through iCloud. These aliases can be used for specific purposes, helping you manage your inbox effectively. Here’s how to create one:
- Go to icloud.com/mail and sign in to your Apple Account if necessary
- Click the gear icon at the top of the Mailboxes list, then choose Settings
- Click Account, then click Add Alias
- Provide the requested information: Alias address – Enter the text to create your alias (e.g., [email protected]). The alias must contain between three and 20 characters; Label – Assign a label for the alias. Aliases are listed alphabetically by their labels; Full Name – Enter the name that will appear in the From field of emails you send using this alias
- Click Create to finalize the alias
- Once created, any email sent to this alias will be forwarded to your primary iCloud email address. For example, if your primary email is [email protected] and you create an alias [email protected], any emails sent to [email protected] will appear in your [email protected] inbox. This allows you to use different addresses for different purposes while keeping everything in one place
It’s important to note that you can still create up to three email aliases through iCloud. Remember that while these aliases provide some flexibility, they do not create separate Apple IDs or completely hide your primary iCloud email address.
Setting up an alias using Apple ID (Kurt “CyberGuy” Knutsson)
BEWARE OF ENCRYPTED PDFS AS THE LATEST TRICK TO DELIVER MALWARE TO YOU
Understanding email aliases
While many email providers offer basic alias functionality, most have significant limitations. Gmail’s “+” addressing and dot tricks, Outlook’s linked aliases and Apple’s iCloud aliases all provide some flexibility, but they often fall short of true privacy protection.
For those of you seeking comprehensive email privacy and robust alias management, my No. 1 pick for private and secure email platforms contains no ads, no tracking and powerful privacy features like password-protected email and unlimited disposable email addresses. See my review of the best secure and private email services here.
How to keep scammers out of your inbox
Protecting your inbox from scammers requires a combination of smart practices and proactive tools. Using email aliases is an effective first step. By creating specific aliases for different activities, such as shopping, subscriptions or work, you can track where spam is coming from and deactivate problematic aliases as needed. Below are some other steps to take.
1. Avoid sharing your primary email address publicly on forums, social media or other platforms to minimize exposure. Most email providers offer robust spam filters, so ensure they are enabled and customize them as needed
GET FOX BUSINESS ON THE GO BY CLICKING HERE
2. Invest in personal data removal services. While no service promises to remove all your data from the internet, having a removal service is great if you want to constantly monitor and automate the process of removing your information from hundreds of sites continuously over a longer period of time. Check out my top picks for data removal services here.
3. Enable two-factor authentication on all your email accounts to add an extra layer of security.
4. Be cautious of suspicious links and attachments. Never click on links or download attachments from unknown senders, as these could be phishing attempts.
5. Use strong antivirus software to protect against potential malware that might come through spam emails. The best way to safeguard yourself from malicious links that install malware, potentially accessing your private information, is to have antivirus software installed on all your devices. This protection can also alert you to phishing emails and ransomware scams, keeping your personal information and digital assets safe. Get my picks for the best 2025 antivirus protection winners for your Windows, Mac, Android and iOS devices.
6. Regularly update your email password and make it strong and unique, avoiding common words or easily guessable combinations. Consider using a password manager to generate and store complex passwords.
These steps will provide a more comprehensive approach to protecting your inbox from scammers and reducing unwanted emails.
SUBSCRIBE TO KURT’S YOUTUBE CHANNEL FOR QUICK VIDEO TIPS ON HOW TO WORK ALL OF YOUR TECH DEVICES
Kurt’s key takeaway
Taking charge of your inbox doesn’t have to be overwhelming. By implementing the tips and tools mentioned above, you’ll create a more secure, efficient and manageable email experience. Whether you’re battling spam or organizing your digital life, email aliases and secure services are great things to put into place.
CLICK HERE TO GET THE FOX NEWS APP
Which email platform do you use most often, and how do you organize your messages there? Let us know by writing us at Cyberguy.com/Contact.
For more of my tech tips and security alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter.
Ask Kurt a question or let us know what stories you’d like us to cover.
Follow Kurt on his social channels:
Answers to the most asked CyberGuy questions:
New from Kurt:
Copyright 2025 CyberGuy.com. All rights reserved.
Kurt “CyberGuy” Knutsson is an award-winning tech journalist who has a deep love of technology, gear and gadgets that make life better with his contributions for Fox News & FOX Business beginning mornings on “FOX & Friends.” Got a tech question? Get Kurt’s free CyberGuy Newsletter, share your voice, a story idea or comment at CyberGuy.com.